Differentiating Key Management Systems & Hardware Security Modules (HSMs)
Key encryption managers have very clear differences from Hardware Security Modules (HSMs.) The main differences reside in how the HSM encryption keys can be used by a Key Manager or HSM. There are other more important differentiators, however, let’s start with how encryption key managers leverage open standards, like the Key Management Interoperability Protocol (KMIP), and what exactly an HSM is.
HSM Key Manager Key Usage – What goes in “Can” Come Out With KMIP
A Key Manager uses a process of administering or managing cryptographic keys for a cryptosystem. A cryptosystem consists of three algorithms: key generation, HSM encryption, and decryption. Key Managers expand full lifecycle of the cryptosystem keys to include protection, storage, exchange, replacement, and use of keys. Key Management Systems focus on the governance of keys as they move through the key lifecycle from creation to activation and use, to revocation, and destruction. Most Enterprise Key Managers utilize KMIP. KMIP is a client/server communication protocol for the storage and maintenance of key, certificate, and secret objects. KMIP is governed by the Organization for the Advancement of Structured Information Standards (OASIS).
HSM Key Usage – Lock Those Keys Down With an HSM
A Hardware Security Module is a secure crypto processor that provides cryptographic keys and fast cryptographic operations. HSM Keys provide storage and protection for keys and certificates which are used to perform fast encryption, decryption, and authentication for a variety of applications. HSM key uses physical tamper resistance and strong authentication. These cryptographic modules provide a greater level of security as they do not have an operating system and are externally attached to the device they are serving. HSM keys can be physically shielded LAN appliances, smart cards, and/or PCI plugin cards, etc. Additionally, they use two-person integrity to protect against internal and external hackers.
Organizations that have modern crypto architected environments utilize both Key Managers and HSMs. What are some of the main points in differentiation between a Key Manager and an HSM encryption?
How Many HSM Encryption Keys Do I Need?
Arguably, the most important differentiator is the number of keys they both support. HSMs have max key limitations in the hundreds and thousands range. Key Managers typically support millions of keys, with the most advanced systems supporting 10s and 100s of millions of keys.
Does HSM Encryption Provide Full Key Lifecycle Support?
An HSM Security essentially creates and protects those keys, and has limitations to the full lifecycle management of those keys outside of the HSM. Key Management Systems actually do full key lifecycle management with protections built around distribution and storage inside and outside the HSM.
Groups and Policy For my Enterprise Key Environment?
Not so much with an HSM encryption, as it typically puts keys in one Security World and has no granular policy engine. This single Security World provides a secure environment for all hardware security devices and key management operations. The Security World is scalable; you can add multiple hardware security devices to a server and share the Security World across multiple servers. Conversely, the most advanced Key Managers can group keys to match your organizational structure, and apply policy to those groups. Some key managers even have hierarchical protection of keys; instead of storing keys in one large security container, keys from one system are not visible to another based on hierarchy.
How do I Put Keys on Varying Systems, Applications, and Devices?
HSM’s default state for a key is non-exportable, making external key management a challenge. HSMs also utilize a protocol called PKCS#11 that is not natively spoken by all systems, apps, or devices. Advanced Key Managers not only integrate with HSMs, but also deliver keys to clients, systems, and locations throughout an environment with KMIP. If a system, app, or device does not speak KMIP natively, some commercially available Key Managers can support key management with translation mechanisms like a REST API.
What are the Benefits of HSM Key Management?
HSMs provide many benefits, including:
- FIPS 140-2 certification (some support level 3 or even level 4)
- Transaction speed
- Designed for security
- Dedicated hardware and software for security functions.
What are the Benefits of a Key Management System?
Key Managers provide many benefits, including:
- FIPS 140-2 certification (Level 1 or Level 2 generally)
- Enables existing products that need keys to use cryptography
- Provides centralized point to manage keys across heterogeneous products.
Why Should I Use Both an HSM and an Encryption Key Manager?
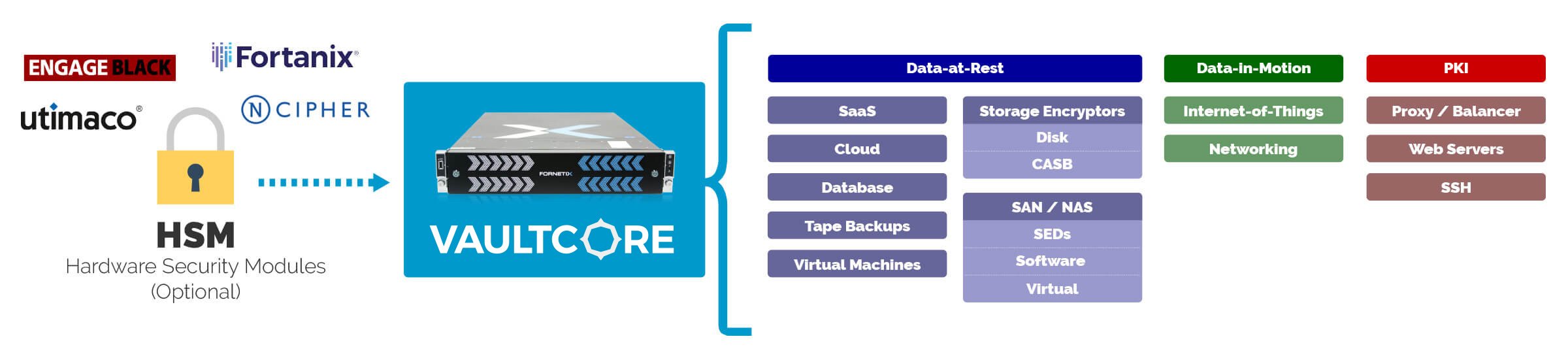
When creating an encryption strategy for your organization, the best thing you can do is leverage both a Key Manager and an HSM. HSM moves the crypto operations to a secure enclave, separating all crypto operations from the application. KMS moves the key governance to a secure enclave, separating out just the key management, allowing the applications to perform their own crypto functions. As seen below in the graphic showing how Fornetix VaultCore works with an HSM when controlling an enterprise encryption’s keys, leveraging both is a feasible and smart solution to deploy in any enterprise organization.
More simply put, the difference between a Key Manager and a HSM is the answer to one question – Who let the keys out (to be easily distributed and managed throughout the rest of the organization)? A Key Manager with KMIP, not an HSM.
In conclusion, even when leveraging an HSM, effective key management is encryption’s biggest roadblock. The idea of encryption is a simple concept, but its implementation on a large scale presents numerous practical challenges.
For effective encryption, key lifecycle processes must be actively managed: generation, registration, distribution, rotation, revocation, suspension, destruction, and storage. Too often, security administrators perform these arduous processes manually and haphazardly. Keys are stored with pen and paper or in Excel spreadsheets, too much data is protected by too few keys, keys are rotated infrequently or not at all.
When your complexity and requirements are exponential for Key Management then the Fornetix VaultCore Appliance offers scalability, ease of use, automation speeds and cost savings to meet your organizational needs.
Want to see how HSMs and VaultCore KMS can help you create an encryption strategy that works the way you need it to? Request a custom demo today.
Note: This entry has been edited to reflect the ‘Key Orchestration’ solution name becoming ‘VaultCore’